The frontline of online piracy liability keeps moving, and core internet infrastructure providers are increasingly finding themselves in the crosshairs.
For rightsholders, site blocking remains the go-to response in many cases. Until recently, the majority of blockades were implemented by consumer ISPs, but expanded legal efforts are now targeting standalone DNS resolvers.
Over the past year, courts in France, Italy, and Belgium have ordered OpenDNS, Cloudflare, and Google to alter their responses to certain DNS queries. Instead of leading visitors to the domains of pirate sites, the companies are required to intercept queries and redirect them elsewhere.
The main rationale for targeting public DNS resolvers is their growing use for bypassing blocking measures rolled out by Internet providers. However, the American tech companies now being targeted are not happy with the role of ‘Internet police’ and appeals of these orders are still pending.
OpenDNS Says Farewell
While these legal battles play out in court, the DNS resolvers still have to comply one way or another. This has resulted in different responses, with Cisco’s OpenDNS taking by far the most drastic action.
When OpenDNS was first ordered to block pirate sites in France, the company made a simple but drastic decision to leave the country entirely, effectively affecting all French users. Last week, it repeated this response in Belgium following a similar court order.
Instead of blocking access to more than 100 sports piracy sites, as the Belgian order requires, OpenDNS announced its departure; at least temporarily.
“Due to a court order in Belgium requiring the implementation of blocking measures to prevent access within Belgium to certain domains, the OpenDNS service is not currently available to users in Belgium,” the company said.
Cloudflare Complies Using ‘Alternate Mechanisms’
Not all DNS resolvers take such drastic measures. Cloudflare chooses to comply with court orders in its own way. Cloudflare DNS (1.1.1.1) users who try to access the targeted domains in countries where blocking orders are issued, see the following notice instead.
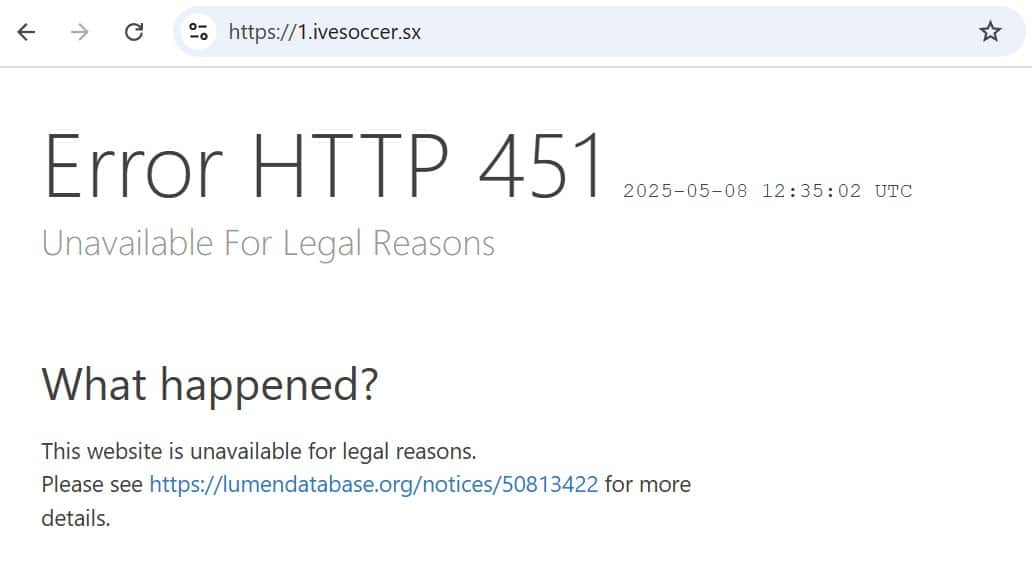
Interestingly, Cloudflare maintains in its transparency report that it is not blocking content through its public DNS resolver. Instead, it points out that it uses “alternate mechanisms”.
“Given the extraterritorial effect as well as the different global approaches to DNS-based blocking, Cloudflare […] identified alternate mechanisms to comply with relevant court orders. To date, Cloudflare has not blocked content through the 1.1.1.1 Public DNS Resolver,” the company writes.

The result for Cloudflare DNS users appears to be the same, however. Those who try to access the blocked domains in the applicable countries will be redirected to the HTTP 451 error.
The good news is that affected users are informed about the reason for this technical blockade via the Lumen Database. That doesn’t appear to be the case with Google.
Google’s DNS Blackout
After running tests in both Belgium and France, using various blocked domains, it’s clear that the targeted websites are no longer accessible through Google’s public DNS resolver (8.8.8.8). However, unlike Cloudflare, there is no notification whatsoever.
Instead, Google appears to simply refuse the DNS query, which means that the domain lookup is not linked to any IP address.
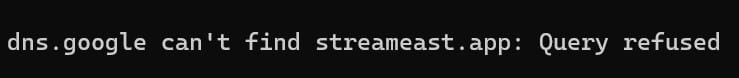
While this is effective in the sense that the pirate sites are no longer available, it’s not very transparent. Users who try to access the domains will simply see a browser error, which could be caused by various DNS issues.
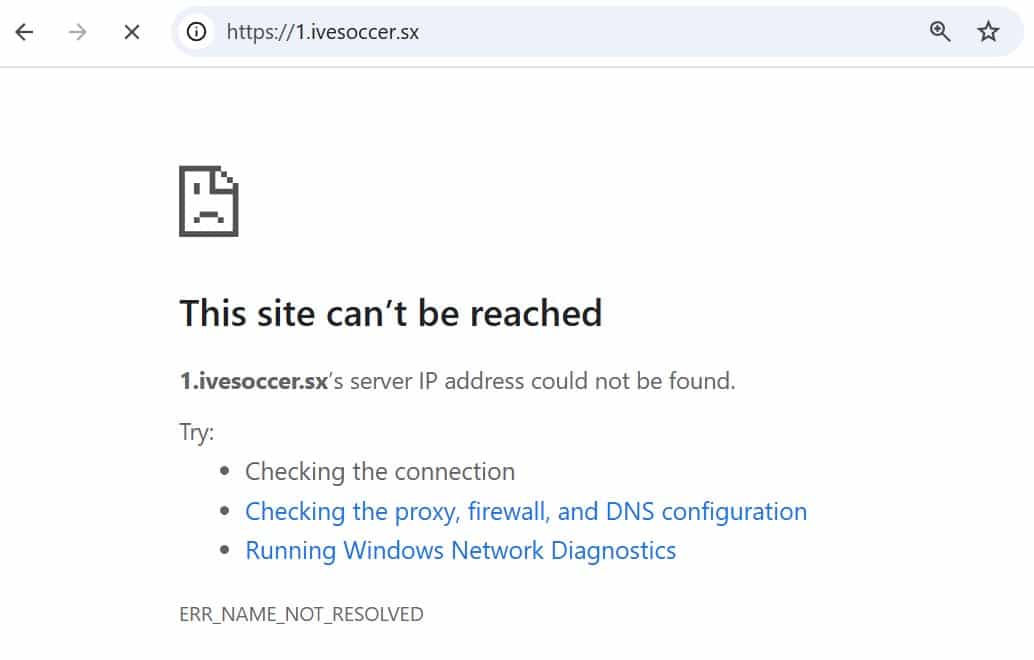
Google’s basic response is not limited to the recent Belgian court order. We observed the same query refusal for domain names that were included in French blocking orders over the past several months.
Transparency is Paramount
While the different responses from DNS resolvers are interesting, Google’s approach doesn’t make blocking efforts more transparent. These orders are still relatively new, so it’s possible that the company is working on offering more transparency in the future, but currently it only adds to the confusion.
Google’s response also appears to go against the advice of the Belgian court, which required the DNS providers to redirect users to a dedicated page, presumably to provide further detail.

If these blocking orders are upheld by various courts, a more streamlined approach will be welcome. Interfering with DNS is a big step that can’t be taken lightly, so transparency is paramount. That’s relevant for the United States too, where a new site-blocking bill also proposes public DNS resolver blockades.
—
For context, a copy of the recent Belgian court order shared by Cloudflare is availablebhere (pdf)
From: TF, for the latest news on copyright battles, piracy and more.
Source : DNS Piracy Blocking Orders: Google, Cloudflare, and OpenDNS Respond Differently








